rad-sbom plugin downloads images from registry APIs and requires authentication for private repositories.
ECR uses short-lived 12-hour tokens, so rad-sbom cannot use standard imagePullSecrets. Instead, an IAM role with the necessary permissions must be attached to the service account named rad-sbom.
Configuring Authentication for ECR
There are two approaches to configure authentication:- EKS Pod Identity - AWS documentation
- IRSA - AWS documentation
IAM Policy
Create an IAM policy with the following permissions:EKS Pod Identity
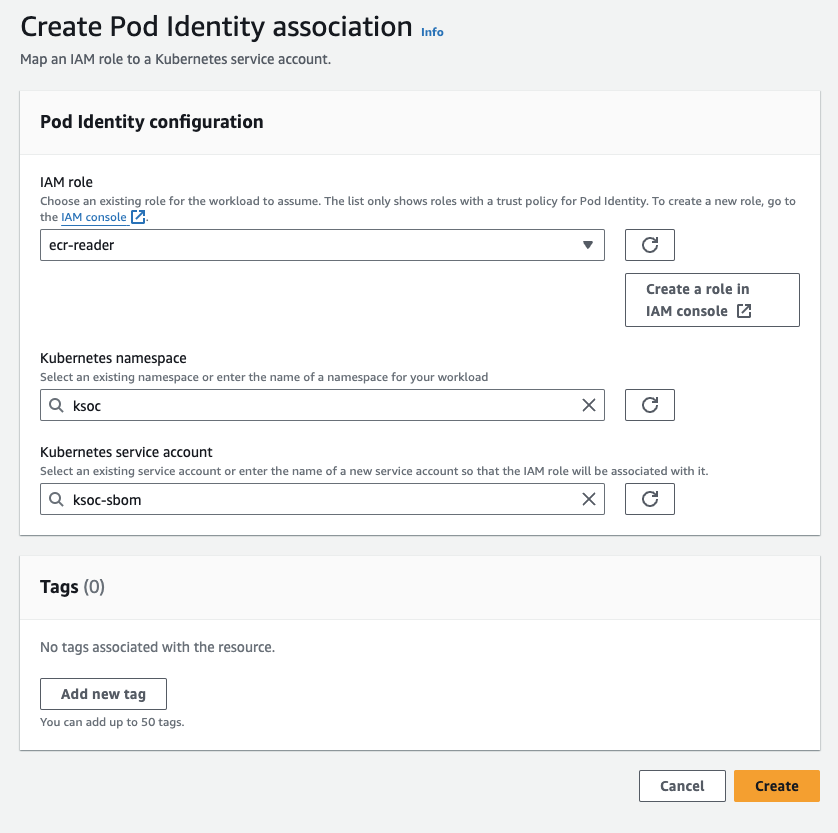
Create a Pod Identity Association for therad-sbom service account:
IRSA
If using IRSA instead of EKS Pod Identity, add the following annotation to yourvalues.yaml: